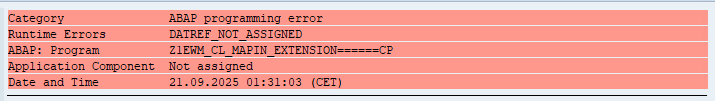
In the world of SAP, runtime errors (also called short-dumps, or simply dumps) are typically viewed as a source of dread and something you should avoid altogether.
The prevailing wisdom is clear:
Catch every exception, log it quietly, and keep the system running without alarming users or halting processes. After all, who wants a production system grinding to a halt over an unhandled issue? But what if this zero-tolerance policy toward dumps is a little too overzealous? What if, in certain scenarios, letting a dump occur isn’t just acceptable but preferable?
In this short article, we’ll explore the nuanced role of dumps in ABAP development, challenging their notoriously bad reputation and shining a light on their often overlooked usefulness and explain why dumps aren’t always the villains they’re made out to be, but actually sometimes they’re the heroes forcing us to confront critical problems as they occur.
Understanding ABAP Short Dumps: The Basics
To appreciate the debate, let’s start with what a short dump actually is. In ABAP, a short dump is essentially a detailed report generated when a runtime error occurs, such as an uncaught exception, an exit message, or a failed assertion.
These runtime errors interrupt the program’s execution and provide a snapshot of the system’s state at the moment of failure. This includes:
- Error type and message
- Source code context
- Call stack
- Variable values at the moment of failure
- User and session information
- System context
- Hints for resolution
In short, a forensic toolkit for debugging.
A primary trigger for such dumps are unhandled exceptions. ABAP offers robust tools like TRY…CATCH blocks to handle exceptions gracefully, allowing developers to log errors, recover where possible, and continue processing.
So, why not always catch and log? As we will see shortly, the answer lies in the context of the error and the value of the information a dump provides.
Why Dumps Have a Bad Reputation
It’s easy to understand why dumps are so disliked:
- User Impact – A dump interrupts a business user’s process with an abrupt error screen. To the end-user, it’s disruptive, confusing, and often frustrating.
- Support Pressure – Dumps are visible in ST22 and usually end up as tickets for the support team. This adds to the operational load and makes it look like the system is unstable.
- Bad Coding Practices – Frequent or poorly handled dumps can be a symptom of sloppy development, where edge cases aren’t accounted for and error handling was an afterthought.
It’s no secret that short dumps carry a stigma in the SAP world. In a culture that values seamless user experiences, dumps are seen as unprofessional.
As one SAP expert on LinkedIn put it, encountering a dump often prompts reactions like, „Who developed this?“—implying incompetence rather than deliberate choice. This knee-jerk negative response overlooks the dump’s strengths, painting it as an outright enemy rather than a tool with situational utility.
The Case For Dumps
Yet, dumps are not inherently bad. In fact, they can be highly useful in certain contexts:
- Maximum Transparency – A dump provides a full context: the exact source code line, the variable values at the time, and a structured call stack. It’s far richer in detail than a simple log entry, which may or may not contain enough clues for debugging.
- Forcing Attention – A log can be ignored. A dump cannot. If a critical piece of logic fails — say, the calculation of pricing, or the assignment of a delivery to a transportation unit — it might actually be better for the system to stop dead in its tracks. That way, the issue is surfaced immediately and with full information, rather than silently creating corrupted or incomplete data.
- Better Than a Silent Failure – Consider the alternative: catching every exception and writing to a log. If no one ever checks that log, the system could keep producing faulty data while the underlying issue goes unnoticed for weeks. A dump, by contrast, guarantees visibility.
Dumps aren’t just errors, they’re information goldmines. Unlike a logged exception, which might be buried in a sea of log files and overlooked during routine monitoring, a dump demands attention. It halts execution of the affected runtime process (not the entire system), alerting users that something has gone fundamentally wrong.
When to Dump, When not to Dump
The art lies in knowing when a dump is acceptable and when it’s not. Here are some guidelines:
- Dump if the failure makes the process result invalid or dangerous to continue. (e.g., missing essential configuration, corrupted master data, or critical calculation failure).
- Log if the error is recoverable, non-essential, or something that the business can still proceed with, perhaps with a warning (e.g., missing optional fields, unrecognized input values that can be skipped).
- Both, if necessary — log details for long-term analysis, but still dump when business-critical integrity is at stake.
This isn’t a call to abandon exception handling. For recoverable errors, like network timeouts or user input issues, TRY…CATCH with logging is ideal, as demonstrated in examples where it prevents unnecessary dumps.
The key is discernment: use dumps strategically for unrecoverable, high-impact failures where the cost of interruption is outweighed by the risk of proceeding.
Conclusion
The blanket statement that “all dumps are bad and should be avoided” misses the purpose and power of dumps.
They are disruptive, yes, but they are also one of the most informative and unambiguous signals a system can give. They enforce accountability on the development side by surfacing issues that must be fixed rather than swept under the rug.
As with most tools, the key lies in balance. Overusing dumps for trivial issues is careless; eliminating them entirely in favor of silent logs is just as risky. Sometimes you need a loud crash to fix what’s broken – and that’s what dumps are good for.
The smartest ABAP developers know when a dump is a safeguard and not a failure and strategically implement them for this purpose.